The PROSA tool and approach
PROSA offers a tool that can be used for evaluating the security of software solutions. This can be used as part of security evaluations, but also for developer support. Modern solutions can have dozens or even hundreds of different servers and protocols in use, which can be impossible for humans to keep sufficiently secure. With the PROSA suite of tools, we can help you both during the development process and with evaluators: We can help you show that your solution is truly secure.
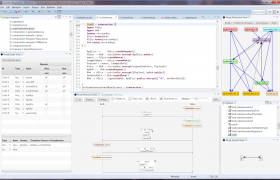
The PROSA security architect
The PROSA security is a tool for supporting the software engineering process of designing security solutions – potentially very large and complex solutions.
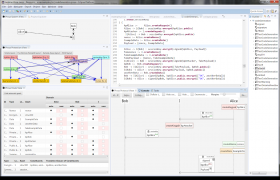
Adding an attack
The tool contains a module that can support the generation of attacks to the design, both automatically and semi-automatic. Passive attacks pattern of arbitrary locations can be generated on single or multiple locations. Active attacks are visualised in the tool similar to the honest (normal) specifications.
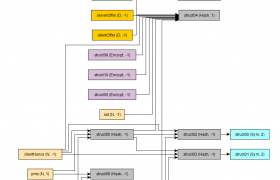
Protection graphs
The protection graph is analysing a complete specification in order to detect all the protection-relations between cryptographic and non-cryptographic assets in the model. Protection graphs also induce an asset hierarchy: starting with the primary assets, then secondary assets – protecting primary assets etc. Protection graphs reveal the inner details of the security design and can reveal several types of design flaws; vicious circles, unprotected cryptographic keys.
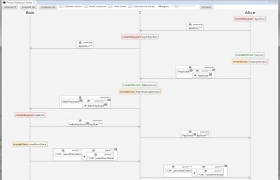
Example sequence diagram
Specifications in PROSA are written in a domain-specific language called ROSA, which instantaneously translates the symbolic specification into a graphical visualization of the corresponding interaction diagram. This makes it easy and convenient for the user to be able to intuitively grasp the behaviour of the specification while writing – not afterwards.
Goals view
The goals view introduces means for specification of security requirements: in particular confidentiality goals and integrity goals. The tool provides a module for automated validation of security goals, by automatically deriving model-generated goals. Deviations between User goals and the generated goals are shown to the User – that should solve these mismatches.
